Trend Micro SecureCloud™ provides data protection for AWS cloud environment. You can deploy SecureCloud as a hosted service (SaaS) or as an on-premise application (inside AWS or in your DC over VPN). Since you can control the keys, it gives you the freedom to encrypt data in in the cloud and have complete control. TrendMicro SecureCloud is available in 32 and 64 bit versions. It currently supports It supports Windows (7, 2003 and 2008), CentOS (5 and 6.0), RedHat (5.4 and 6.0), Ubuntu (9.10 and above), Amazon Linux (09.11 and above), SUSE Linux Enterprise 11. I have tested RHEL on 6.2. Let us explore in this article how to secure the EBS using SecureCloud.
Step 1: Create an EBS volume
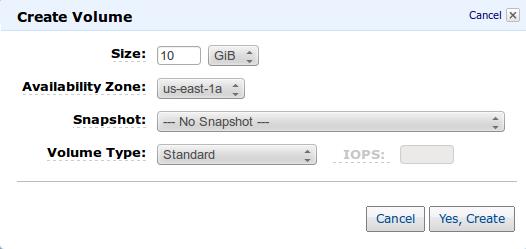
First step is to create an empty EBS volume, You can use Amazon Console to create an 10 GiB EBS volume as stated in following diagram.
Please do not attach the EBS Volume with the EC2 Instance. We will see as the article progresses how Trend Micro Secure cloud
will attach this.
Download the latest version of TrendMicro SecureCloud
from the http://downloadcenter.trendmicro.com/.
Please change the version numbers accordingly. Sample Reference Command
# wget
http://www.trendmicro.com/ftp/products/securecloud/scagent-<version>.x86_64.bin
|
Step 3: Install TrendMicro SecureCloud
After the TrendMicro SecureCloud installer is downloaded, give necessary permissions for the same.Install TrendMicro SecureCloud using command:
#
./scagent-<version>.x86_64.bin
|
Run the configuration utility, accept the
license agreement and choose Cloud Service Provider (CSP) plugin
#
sh /var/lib/securecloud/scconfig.sh
|
Since you are configuring TrendMicro
SecureCloud to protect your AWS EBS Volumes, Please enter “Amazon-AWS” as Cloud Service Provider,
Once the Cloud Service Provider is
selected, Please Enter following details
- Access Key ID
- Secret Access key ID
- SecureCloud Management Server Access ID : You can get the Access ID by following the below steps:
Logon to TrendMicro Web console, go to the administration panel and select User Management option.
Get the Account ID from the Console.
TrendMicro SecureCloud Management Server Web Service URL
If you are using SaaS version of TrendMicro SecureCloud, then leave the field blank.
In case if you are using on-premise version of TrendMicro SecureCloud Management Server, then give the full URL.
SecureCloud Management Server Provision Passphrase
Get the Provision passphrase from Console.
Do you want to update inventory? [Yes or No] – Yes: This option will update and upload list of images and volumes from AWS to TrenMicro SecureCloud management server.
Do you want to wait for provisioning? [Yes or No]- Yes: Whenever you want to provision an EBS Volume for encryption, you need to select this option.
Timeout setting (minute) for provisioning process? Default is 10 Minutes.
Do you want to get mount device list? - Yes: This option will get you the list of volumes with their mount points.
Once the above details have been configured, TrendMicro SecureCloud provisioning utility will start uploading the inventory. Once the inventory is uploaded, we can see list of all images and devices in TrendMicro SecureCloud web console by selecting inventory section. In the image below, we can see device status as “Not Configured”.
Immediately after uploading inventory, volume
provisioning utility will start.
Once the provision utility starts in the console, Please go to TrendMicro SecureCloud web console and select inventory->devices section. Select the device/volume you want to encrypt.
Step 6: Configure the device details
Please fill values for the following parameters:
Platform and File system – Linux and File System can be ext3/4, XFS etc.
Write Access: Volume will be used for read or read/write purpose. Set the value as “Read/Write”.
Mount point: Volume mount point in the Amazon EC2 instance. Set the value as “/EBS”.
Image Identity - The Amazon EC2 instance to which you want to attach this volume
Once the above values are configured in the
TrendMicro Console, you observe that the device status has got changed from
“Not Configured” to “Configured”. (Refer
the picture below)
Select the ‘configured’ device and choose the “Encrypt”
option.
Since encryption of the device is a destructive
process which erases any data residing on the device, it asks for an acknowledgement
from the user. On pressing ok option the encryption process will start and the
device status will change from ‘Configured’ state to ‘Encrypting’ state. You
can observe the progress of this process on the terminal window. Once the encryption process is over, you can
observe that the device state is in ‘Encrypted’ state in the TrendMicro
Console.
After all the devices are provisioned, you can stop
provisioning utility or wait for timeout.
Once the provisioned utility is stopped, we will receive the mount list
and script will end.
#service scagentd start
|
Once the service is started, key exchange
will happen between TrendMicro SecureCloud management server and TrendMicro SecureCloud
agent on the AWS. There are two ways the key exchange can be approved.
Manual Key Approval
In this model, whenever TrendMicro SecureCloud agent service is stopped
and started, we need to go to running instances section and approve pending
key. After approval, the volume will be mounted on Amazon EC2 instance and
ready for use. Once the volume is mounted on EC2 instance, the device status
will change from ‘Encrypted’ state to ‘In-Use’ state.On
the approve button is pressed, the keys will be approved and delivered. (Illustrated
in the below image)
Now, on issuing ‘mount’ command on instance, we can see that the volume is mounted on the mentioned mount point and ready for use.
Automatic Key Approval
Manually approving key is not an attractive option for large AWS deployments. You can approve key automatically based on pre-defined user policies as well using TrendMicro SecureCloud. For example: You can have policy which says approve key request from a particular IP address or IP range or approve key request from all EC2 instances which have their mount point as /EBS etc. Go to policies section in TrendMicro console to configure policies. Every device/volume can be associated with a policy. In the below diagram, we have defined policy to approve key request from all instances which have device mount point as /EBS (sample).
Part 1: Understanding Amazon Elastic Block Store
Part 2: Understanding Standard EBS Volumes
Part 3: Understanding EBS PIOPS Volumes
Part 4: Understanding EBS-Optimized Instances
Part 5: Understanding Latency in EBS
Part 7: 10% of your provisioned IOPS 99.9% of the time
Part 8: Performance Tuning - Pre Warming the EBS volume
Part 9: Performance Tuning - EBS Striping
Part 10: Performance Tuning - IO Block Size
Part 11: Understanding Amazon EBS Snapshots
Part 12: Securing Amazon EBS volumes - EBS Encryption using SecureCloud
Part 13: Amazon EBS Security Best practices and tips











No comments:
Post a Comment